


IT Audit Services
IT Audit is the process of collecting and evaluating evidence to determine whether a computer system has been designed to maintain data integrity, safe guard assets, allow organizational goals to be achieved effectively, and use resources efficiently. Data integrity relates to the accuracy and completeness of information as well as to its validity in accordance with the norms. An effective information system leads the organization to achieve its objectives and an efficient information system uses minimum resources in achieving the required objectives. IT Auditor must know the characteristics of users of the information system and the decision making environment in the auditee organization while evaluating the effectiveness of any system.

ITIS’s Information Technology (IT) Audit professionals help organizations gain insight into the threats inherent in today’s highly complex technologies.
Our approach in IT audit appropriately assesses technology risks and the control environment as they relate to critical business processes. ITIS's deep expertise in IT audit can help ensure the integrity, reliability and performance of these processes. Through our methodologies, our clients realize more effective and efficient technology controls that better align the internal audit function with their business and IT strategies.
Penetration Test Service
A penetration test is a method of evaluating the security of a computer system or network by simulating an attack from a malicious source, known as a Black Hat Hacker, or Cracker. The process involves an active analysis of the system for any potential vulnerabilities that may result from poor or improper system configuration, known and/or unknown hardware or software flaws, or operational weaknesses in process or technical counter measures. This analysis is carried out from the position of a potential attacker, and can involve active exploitation of security vulnerabilities. Any security issues that are found will be presented to the system owner together with an assessment of their impact and often with a proposal for mitigation or a technical solution. The intent of a penetration test is to determine feasibility of an attack and the amount of business impact of a successful exploit, if discovered. It is a component of a full security audit.

BG Tech follows a structured approach based on best practices and well-developed methodologies to ensure objectives are met. BG Tech approach to ethical hacking service(PT) is based on a combination of in-depth methodologies and continual innovation to ensure a thorough check of the customer’s network for vulnerabilities.
BG Tech IT Solutions proposes the following service to meet the objective of the customer.
Penetration Testing by BG Tech is a systematic and structured high-end analysis, testing and reporting exercise conducted in order to:
Black Box Penetration Test (Ethical Hacking Service) cycle would pass through a series of tasks, specially designed to identify the security vulnerabilities in assets exposed to the public domain. Every stage of the methodology generates an output that may serve as a piece of information for individual reporting or as input for a subsequent task.
Black Box Penetration Test (Ethical Hacking Service) comprises five phases.
Network Surveying: This step involves gathering the customer’s information pertaining to the public domain through web sites, mail servers, public records and databases. This allows the PT team to discover and enumerate the target systems to be tested.
Port Scanning: Port scanning is the process of probing system ports on the transport and network layer of the target systems. Port scanning is used to enumerate live or accessible Internet services. Here, the scan is run in various modes such as connect, SYN, FIN, Xmas, Null, UDP, and FTP Bounce to identify the operating system, version and lists of services running on a target host.
System Finger-printing: System finger-printing is the process of probing target systems to confirm host operating systems and version levels. This process also gathers other explicit and implicit information about target systems.
Router ACL, Firewall Testing: This step involves using different methods to discover the routers and firewalls (from default ports, IP stack and TCP/IP fingerprinting). The BG Tech team will also use various techniques and tools to attempt the penetration of the firewall to reach target hosts.
In this phase, the BG Tech PT team identifies, understands and verifies the weaknesses, misconfigurations and vulnerabilities of target hosts and maps the profile of the environment with the information gathered. This task involves:
The BG Tech team will use various commercial/non-commercial/proprietary tools to discover and enumerate vulnerabilities at different levels such as OS, Services & Applications.
Attempting Brute Force: The BG Tech team will run various brute-force attacks to attempt the acquisition of passwords and discover weak passwords of Applications, Services and OS accounts.
IP Attacks: In this step, the BG Tech team will run various DOS, DDOS and other attacks on discovered and enumerated services.
Following points are valid if fully exploited
Gaining Access to Target Hosts: Based on the vulnerabilities enumerated in Phase 2, the BG Tech team will attempt the exploitation of these vulnerabilities to gain unauthorized access to target hosts.
Leaving Traces: Dependent on the success of each exploit, the BG Tech team will leave traces as proof of compromise, wherever possible.
Privilege Escalation: Dependent on the success of the BG Tech team’s gaining valid user access, all possible privilege escalation will be attempted and documented.
Web Application Code Audit Service
BG Tech adopts a static source code analysis platform that leverages third generation software verification technologies to identify web application vulnerabilities throughout development. Our web-based solution provides automated compiler-independent code analysis that models tainted data flow within the application. Reports pinpoint vulnerable code locations and offer prioritized remediation guidance, while integration facilitates immediate hot-fix remediation. Our service offers proactive and cost-effective remediation for vulnerable code, representing a low-cost, risk-free alternative to the common build-first secure-later paradigm.

BG Tech follows a structured approach based on best practices and well-developed methodologies to ensure objectives are met. BG Tech approach to ethical hacking service(PT) is based on a combination of in-depth methodologies and continual innovation to ensure a thorough check of the customer’s network for vulnerabilities.
DRP & Implementation Services
A disaster recovery plan (DRP) - sometimes referred to as a business continuity plan (BCP) or business process contingency plan (BPCP) - describes how an organization is to deal with potential disasters. Just as a disaster is an event that makes the continuation of normal functions impossible, a disaster recovery plan consists of the precautions taken so that the effects of a disaster will be minimized and the organization will be able to either maintain or quickly resume mission-critical functions. Typically, disaster recovery planning involves an analysis of business processes and continuity needs. Disaster recovery services can help companies recover from virtually any type of disaster and ensure ongoing availability of mission-critical resources.
As IT is increasingly being applied to the core of business, availability of Business Application Service and IT infrastructure are critical for organizations to conduct its business functions, and DR and contingency planning process helps in ensuring high availability and reduces the risk of business interruption.
The process itself can lead to significant improvements in business operations by identifying points of failure and making improvements in business process.
Development of DR capabilities is the key project is to be undertaken by the infrastructure group, along with other initiatives suggested.
The recovery time objective (RTO) is the maximum allowable downtime after an outage for recovering systems, applications, and functions. RTO provides the basis for developing cost-effective recovery strategies and for determining when and how to implement these recovery strategies during a disaster situation. The recovery point, for example, defines how current the data is after a disaster.
The recovery point objective (RPO) is the earlier point in time to which systems and data must be recovered after an outage. RPO defines the maximum amount of data that your organization is willing to sacrifice after a disaster; i.e. a zero RPO business continuance solution can survive a disaster without any loss of data. Together, RTO and RPO provide a measurable target for your business continuance and disaster recovery solution to achieve. Improving RTO and RPO requires increasing your investment in networking and storage technologies and processes. Also, the physical distance between your data centers and how well your applications tolerate network latency affects how close you can get to zero RPO. That is why you should limit your RTO and RPO to whatever levels your organization can effectively tolerate.
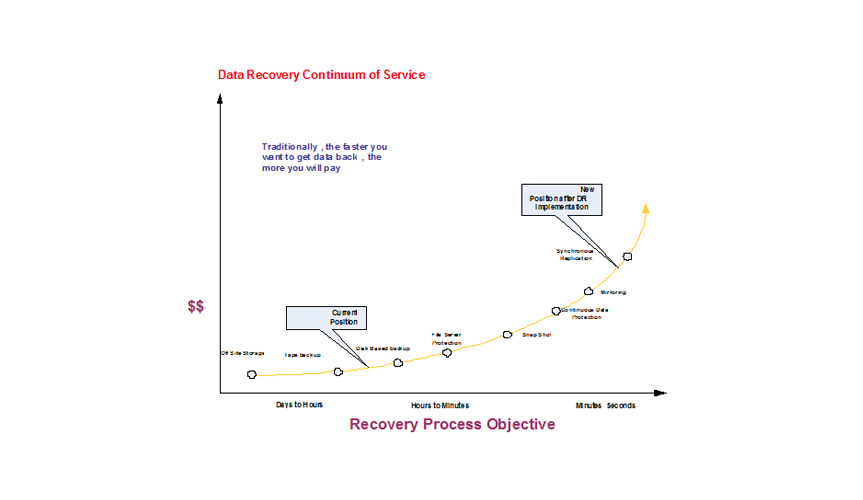
We propose business group develop a strategic initiative to design a disaster recovery and business contingency plan to ensure the business systems and infrastructure availability.
We recommend following structured methodology based on federal guidelines to design, develop, deploy, test and maintain DR/Contingency Planning programs.
We can assist organizations in development and integration of a series of procedures that direct the actions of personnel within a business unit, at the time of a business interruption, to minimize the impact of the business interruption and to achieve a timely continuation or resumption of business activities.
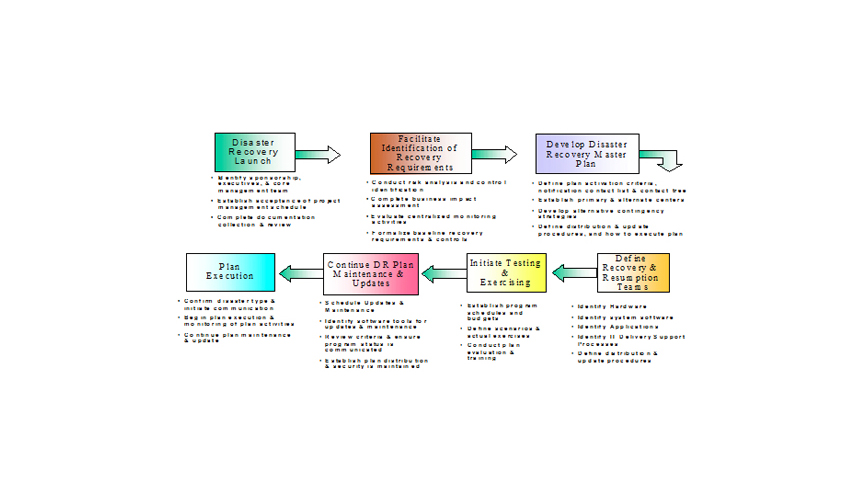
The figure shows the process that we can follow to develop a DR and Contingency Planning program for organisations. Over all the key elements of the process are as follows:
We will help Organizations identify a location and set up DR capability so as to free up much needed space for other business units to operate from HQ.
Identify facilities that are located in geographically separate regions that can be used to deliver and support IT services. Each location can serve as a backup facility for other facilities. We will propose a detailed DR response plan and implement the plan and the required infrastructure after we conduct a detailed assessment of the requirements and various options that are available to business.
IT Security Policy Development
Information Security Policies are the cornerstone of information security effectiveness. The Security Policy is intended to define what is expected from an organization with respect to security of Information Systems. The overall objective is to control or guide human behavior in an attempt to reduce the risk to information assets by accidental or deliberate actions. Information security policies underpin the security and well-being of information resources. They are the foundation, the bottom line, of information security within an organization.
This policy should covers all information and information resources, including computers and communication devices owned or operated by organizations as well as information stored on a remote system operated by an outside entity. This policy should also cover any computer or communications device that is present on organizations premises and/or use organization communication infrastructure, but which may not be owned or operated by organizations. Information includes data stored on magnetic or other electronic media, data stored in computer memory, data displayed on a monitor, projector system or other output, data being transmitted over communication lines or verbal, written or printed documents.